...
These are the steps that need to be completed for the certificate hierarchy:
Generate Root Certificate
Generate a private key file (ca.key) for the Root CA using the command below. You may choose to enter a passphrase to be associated with the ca.key file as well.
| Tip |
|---|
| Make note of this passphrase if you set one for the Root CA private key file (ca.key) as it will be used multiple times. |
| Code Block |
|---|
openssl genrsa -des3 -out ca/ca.key 4096 |
Generate a self-signed certificate (ca.crt) for the Root CA using the command below. This command generates a new self-signed X.509 certificate named "ca.crt" valid for 3650 days (10 years) using the RSA private key "ca.key". You will be required to enter the pass phrase associated with the private key file "ca.key".
| Code Block |
|---|
openssl req -new -x509 -key ca/ca.key -days 3650 -out ca/ca.crt |
| Note |
|---|
| There are a number of fields associated with the creation of the certificate. Fill them out with your relevant details. |
| Code Block |
|---|
|
$ openssl req -new -x509 -key ca/ca.key -days 3650 -out ca/ca.crt
Enter pass phrase for ca/ca.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:KS
Locality Name (eg, city) []:Stilwell
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Cirrus Link Solutions
Organizational Unit Name (eg, section) []:Support
Common Name (e.g. server FQDN or YOUR name) []:CLS Example Root CA
Email Address []:
$ |
Azure will need the certificates in PEM format. Convert the CRT format to PEM format using the command below.
| Code Block |
|---|
openssl x509 -in ca/ca.crt -out ca/ca.pem -outform PEM |
...
| Note |
|---|
| Depending on the version of openSSL that you are using, you may see additional .srl files created which contain the signed certificate's unique serial number. These files are not used directly by the modules and not included in the certificate hierarchy displayed above. |
Generate Device Certificate
Generate private key in PSCK8 format (CertDevice.key) for the device using the command below.
| Code Block |
|---|
openssl genrsa -out certs/device/CertDevice.key 4096 |
Generate a Certificate Signing Request (CSR) for the device using the command below. This command generates a new CSR named "CertDevice.csr’ using the RSA private key "CertDevice.key".
| Code Block |
|---|
openssl req -new -key certs/device/CertDevice.key -out certs/device/CertDevice.csr |
| Note |
|---|
| There are a number of fields associated with the creation of the certificate. Fill them out with your relevant details. |
| Code Block |
|---|
| title | Example Device CSR Creation |
|---|
|
$ openssl req -new -key certs/device/CertDevice.key -out certs/device/CertDevice.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:KS
Locality Name (eg, city) []:Stilwell
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Cirrus Link Solutions
Organizational Unit Name (eg, section) []:Support
Common Name (e.g. server FQDN or YOUR name) []:Device01
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []: $ |
| Warning |
|---|
| The Common Name or FQDN must match the name of the logical Device Id in IoT Hub. In our example the Device Id is Device01 |
Sign the Device CSR with the Device CA using the command below. This command will sign the CSR "CertDevice.csr" with the Root CA certificate ‘ca.crt’ and Root CA's RSA private key ‘ca.key’, creating a new X.509 certificate named ‘CertDevice.crt’ valid for 365 days (1 year). You will be required to enter the passphrase associated with the private key file "ca.key".
| Code Block |
|---|
openssl x509 -req -in certs/device/CertDevice.csr -CA ca/ca.crt -CAkey ca/ca.key -CAcreateserial -out certs/device/CertDevice.crt -days 365 |
Azure will need the certificate in PEM format. Convert the CRT format to PEM format using the command below:
| Code Block |
|---|
openssl x509 -in certs/device/CertDevice.crt -out certs/device/CertDevice.pem -outform PEM |
...
iotcerts/
├── ca/
│ ├── ca.crt
│ ├── ca.pem
│ ├── ca.key
└── certs/
├── device/
├── CertDevice.crt
├── CertDevice.pem
├── CertDevice.csr
└── CertDevice.key
Add Root Certificate to IoT Hub
- On the IoT Hub resource Overview page, click “Certificates” menu on the left blade, and click the “Add” button.
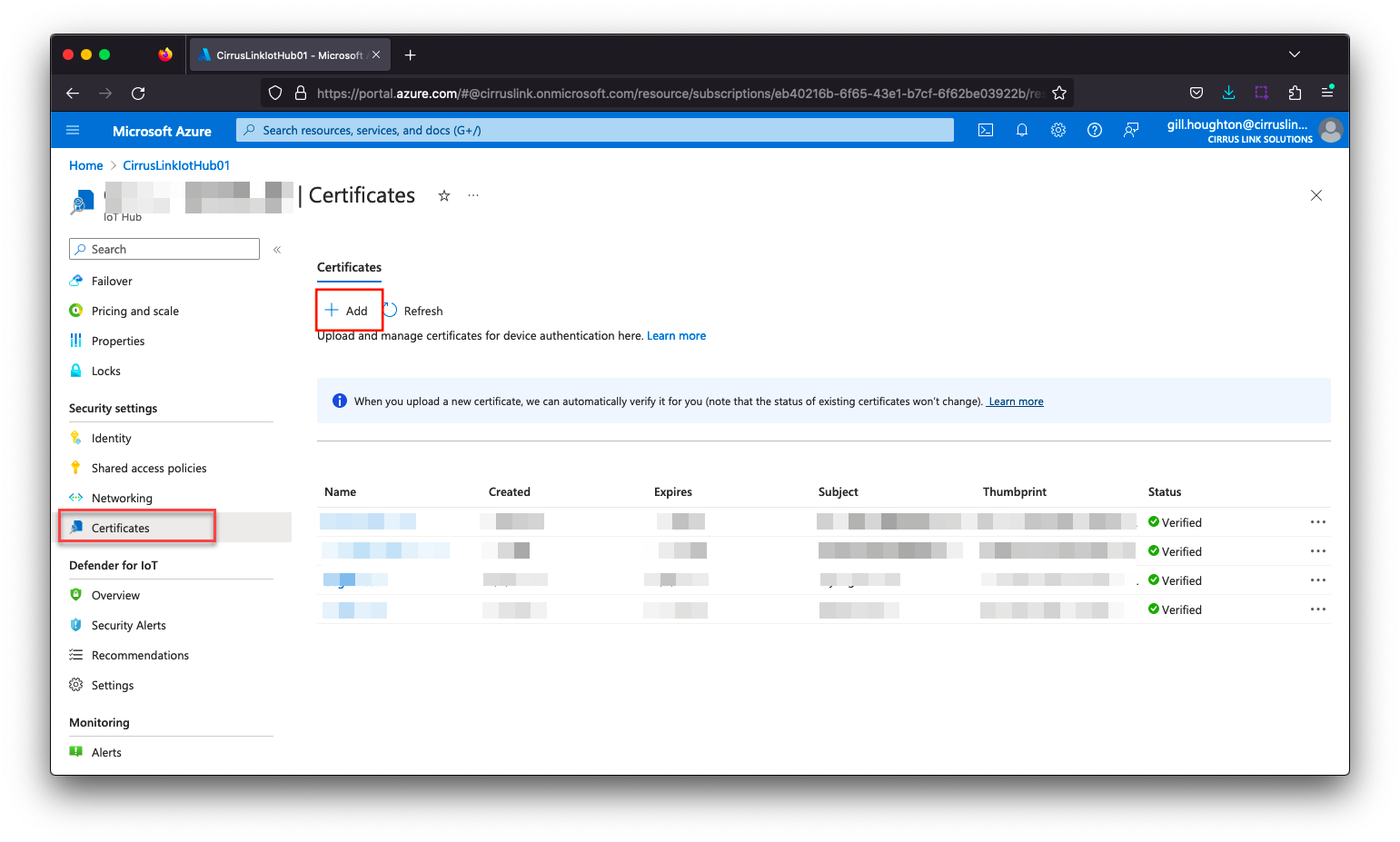
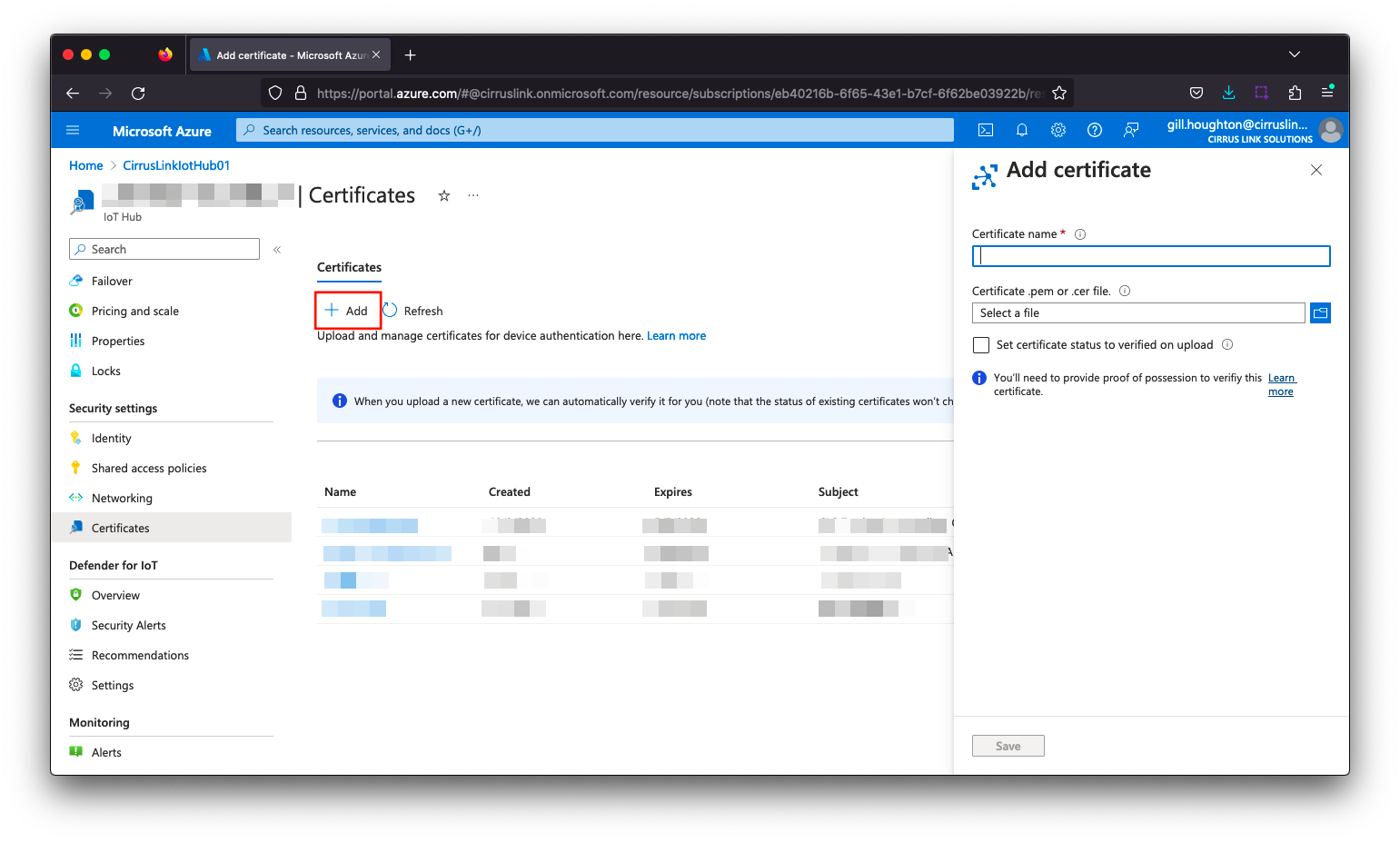
- Give a certificate name (eg. MyOrg RootCertificate) and import the ca.pem file from your iotcerts/ca folder. Check the “Set certificate status to verified on upload” checkbox and click Save.
Add device certificates to Azure Injector IoT Hub configuration
Navigate to the Azure Injector > Settings > Azure IoT Hubs > Certificates and add the certificates as shown below:
...
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()