![]()
Page History
...
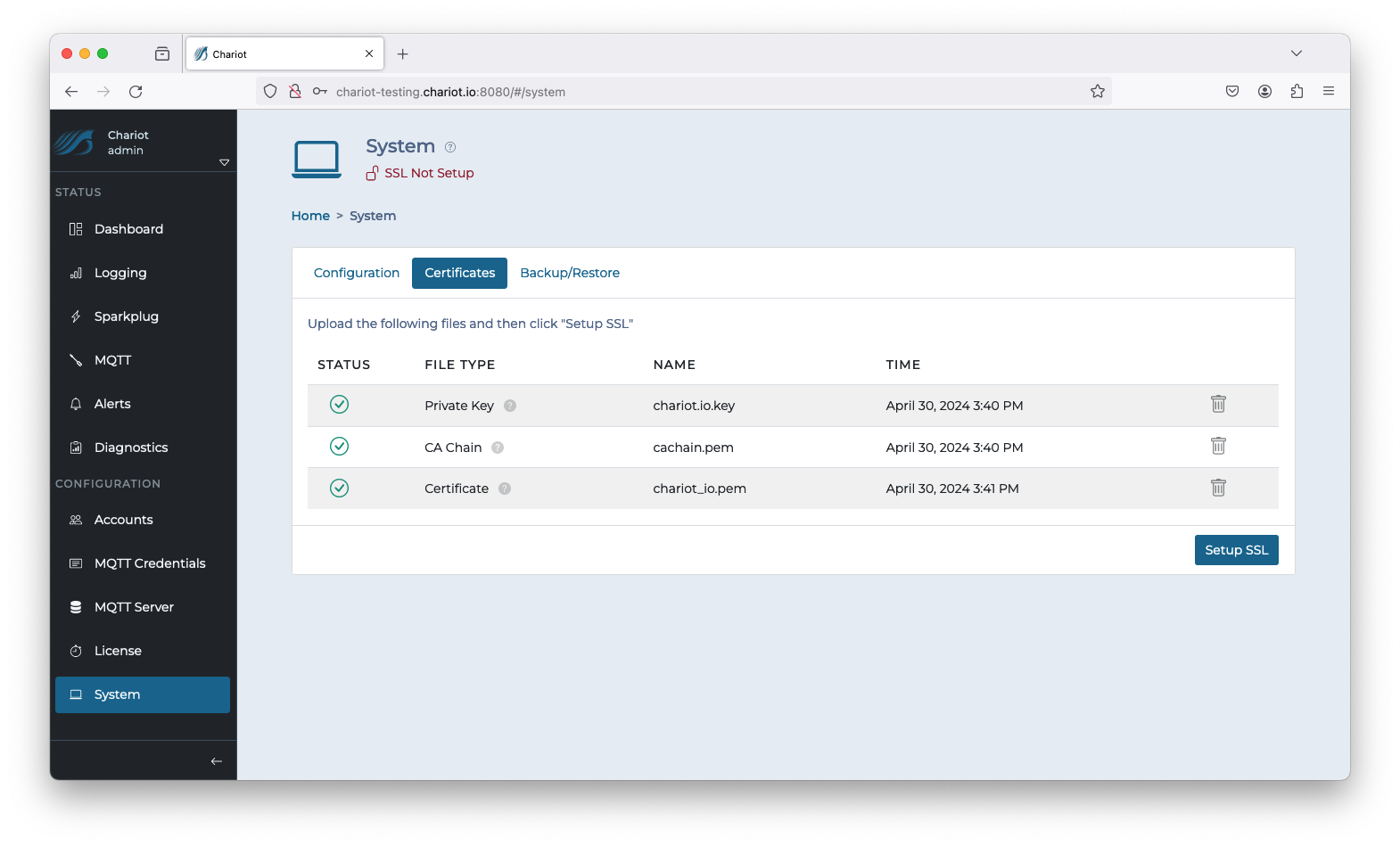
| File Type | Where to get the file |
|---|---|
| CA Chain | Provided by your Certificate Authority |
| Private Key | The key you generated when creating your CSR to submit to your CA |
| Certificate | The server certificate provided by your Certificate Authority after you submitted your CSR to them |
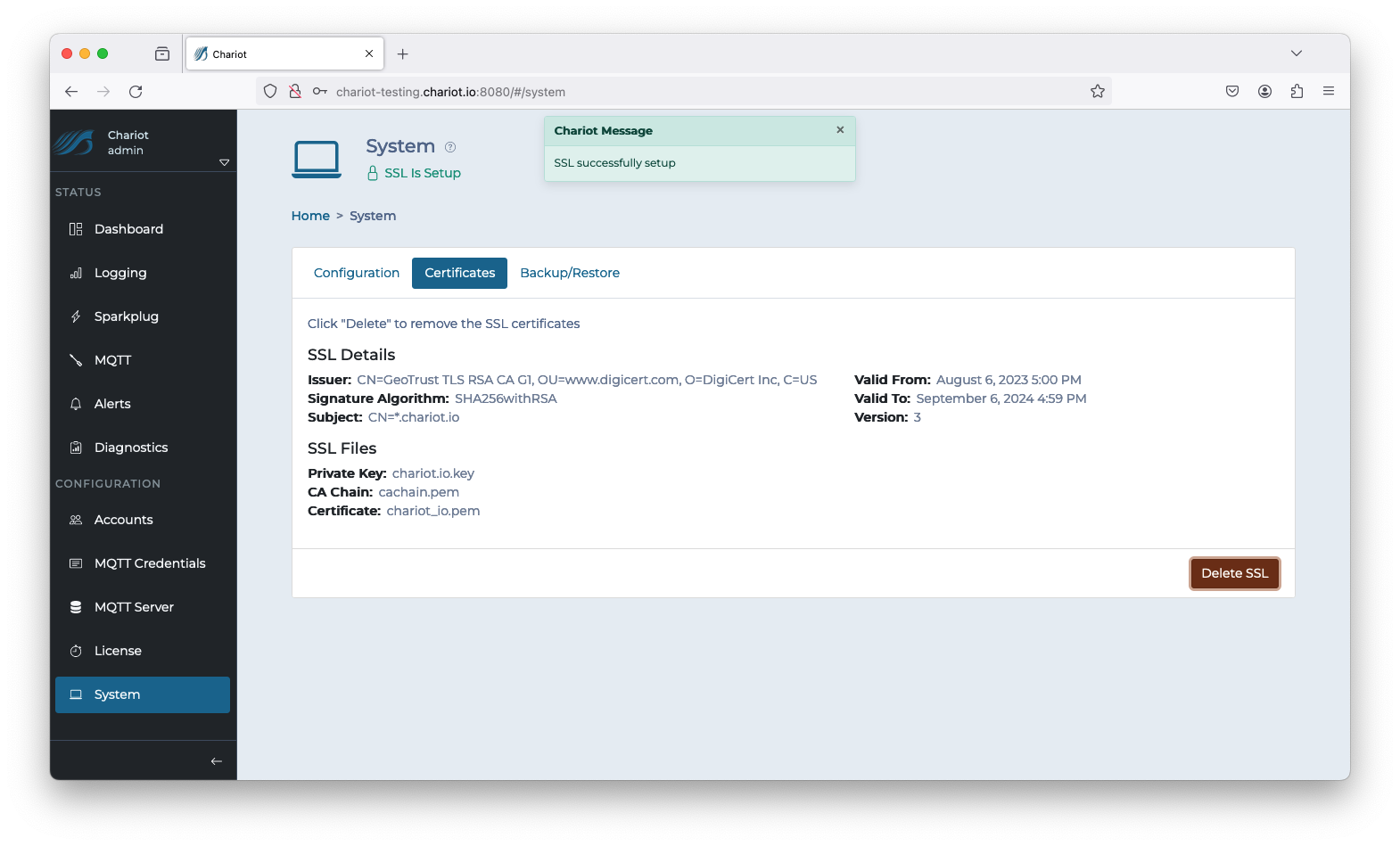
Navigate to CONFIGURATION > MQTT Server configuration and Enable Secure as shown below. Select the Update button to save the configuration.
...
You will see that the truststore contains no entries.
Use the following command to add the Engine client side Root CA certificate to the truststore using the "trustStorePassword" when prompted.
When prompted Trust this certificate? [no]: respond respond "yes"
| Code Block | ||
|---|---|---|
| ||
keytool -importcert -file ca/engine/engineca.crt -keystore <chariot_install_dir>/security/clientcerts.jks -alias EngineDeviceCACertificate |
Use the following command to add the Transmission Engine client side certificate to the truststore using the "trustStorePassword" when prompted.
When prompted Trust this certificate? [no]: respond respond "yes"
| Code Block | ||
|---|---|---|
| ||
keytool -importcert -file cacerts/transmissionengine/transmissionCAengine.crt -keystore <chariot_install_dir>/security/clientcerts.jks -alias TransmissionDevice1 |
...
EngineDevice |
Use the following command to add the Transmission client side certificate to the truststore using the "trustStorePassword" when prompted.
When prompted Trust this certificate? [no]: respond "yes"
| Code Block | ||
|---|---|---|
| ||
keytool -importcert -file certs/transmission/transmission.crt -keystore <chariot_install_dir>/security/clientcerts.jks -alias TransmissionDevice1 |
Once completed, viewing the file will now show three entries similar to below:
| Code Block | ||
|---|---|---|
| ||
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 3 entries
Alias name: cacertificate | ||
| Code Block | ||
| ||
Keystore type: PKCS12 Keystore provider: SUN Your keystore contains 2 entries Alias name: enginedevice Creation date: Feb 7, 2024 Entry type: trustedCertEntry Owner: CN=EngineDeviceCLS Example Root CA, OU=Support, O=Cirrus Link Solutions, L=Stilwell, ST=KS, C=US Issuer: CN=CLS Example Root CA, OU=Support, O=Cirrus Link Solutions, L=Stilwell, ST=KS, C=US Serial number: 6f689c58c0f3e7177224c5868b75fcd51bcc2e0f Valid from: Wed Feb 07 19:43:45 UTC 2024 until: Sat Feb 04 19:43:45 UTC 2034 Certificate fingerprints: SHA1: 15:BC:A7:28:BE:15:D9:7F:E7:B0:1E:51:4E:A0:0F:57:58:C7:A3:2E SHA256: 7A:1E:A0:D8:B5:4E:CB:BF:2D:A9:8D:E2:7F:E6:20:3C:B8:2C:11:4F:14:FF:AD:F6:A1:01:58:C0:37:B3:04:A7 Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 4096-bit RSA key Version: 3 ******************************************* ******************************************* Alias name: transmissiondevice1enginedevice Creation date: Feb 7, 2024 Entry type: trustedCertEntry Owner: CN=TransmissionDevice1EngineDevice, OU=Support, O=Cirrus Link Solutions, L=Stilwell, ST=KS, C=US Issuer: CN=CLS Example Root CA, OU=Support, O=Cirrus Link Solutions, L=Stilwell, ST=KS, C=US Serial number: 6f689c58c0f3e7177224c5868b75fcd51bcc2e116f689c58c0f3e7177224c5868b75fcd51bcc2e0f Valid from: Wed Feb 07 19:5243:4845 UTC 2024 until: ThuSat Feb 0604 19:5243:4845 UTC 20252034 Certificate fingerprints: SHA1: 6015:7EBC:A5A7:6E28:47BE:0915:79D9:FB7F:A9E7:FEB0:241E:DB51:054E:1EA0:090F:5457:2458:48C7:19A3:BD2E SHA256: 8A7A:1E:C8A0:39D8:E1B5:504E:8BCB:BF:352D:25A9:438D:C7E2:B47F:66E6:6020:023C:1EB8:AF2C:11:4F:C414:11FF:32AD:B0F6:6DA1:FC01:6D58:6EC0:5D37:A8B3:BE:FA:00:0B04:A7 Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 4096-bit RSA key Version: 3 ******************************************* ******************************************* |
...
Alias name: transmissiondevice1
Creation date: Feb 7, 2024
Entry type: trustedCertEntry
Owner: CN=TransmissionDevice1, OU=Support, O=Cirrus Link Solutions, L=Stilwell, ST=KS, C=US
Issuer: CN=CLS Example Root CA, OU=Support, O=Cirrus Link Solutions, L=Stilwell, ST=KS, C=US
Serial number: 6f689c58c0f3e7177224c5868b75fcd51bcc2e11
Valid from: Wed Feb 07 19:52:48 UTC 2024 until: Thu Feb 06 19:52:48 UTC 2025
Certificate fingerprints:
SHA1: 60:7E:A5:6E:47:09:79:FB:A9:FE:24:DB:05:1E:09:54:24:48:19:BD
SHA256: 8A:C8:39:E1:50:8B:BF:35:25:43:C7:B4:66:60:02:1E:AF:4F:C4:11:32:B0:6D:FC:6D:6E:5D:A8:BE:FA:00:0B
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 4096-bit RSA key
Version: 3
*******************************************
******************************************* |
| Anchor | ||||
|---|---|---|---|---|
|
Using a text editor, set the "clientAuthPolicy" to "required" in the <chariot_install_dir>/conf/com.cirruslink.chariot.server configurationfile.
| Code Block | ||
|---|---|---|
| ||
clientAuthPolicy="required" |
| Warning |
|---|
| You will now need to restart the Chariot service to pickup up the configuration changes |
| Anchor | ||||
|---|---|---|---|---|
|
Anchor MQTTEngineClientSide MQTTEngineClientSide
MQTT Engine Client Side Configuration
| MQTTEngineClientSide | |
| MQTTEngineClientSide |
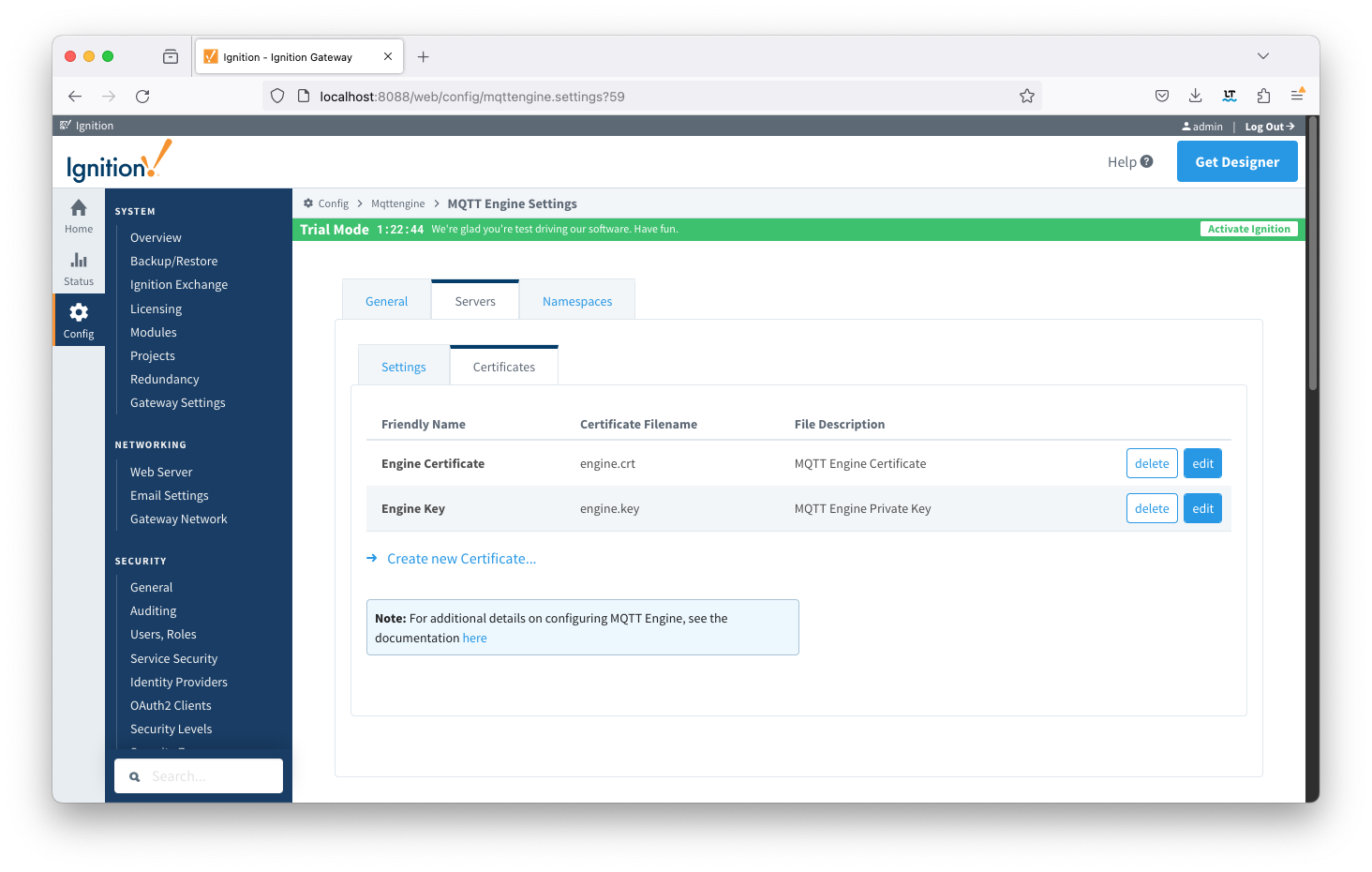
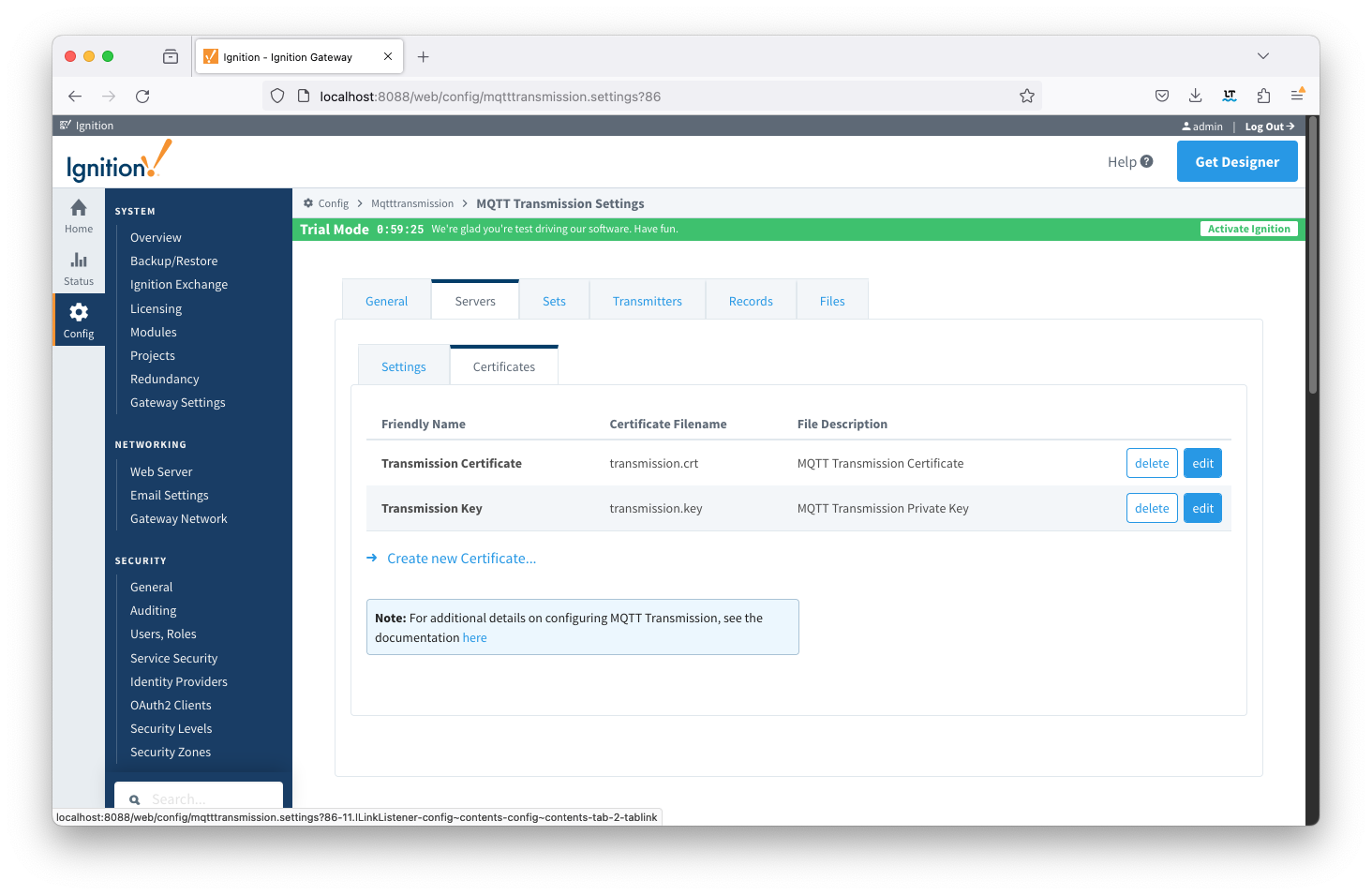
Add the certificates to the MQTT Engine > Servers > Certificates configuration as shown below:
Friendly Name | Certificate Filename | File Description | File Location |
EngineCertificate | engine.crt | MQTT Engine Certificate | chariotcerts/certs/engine |
EngineKey | engine.key | MQTT Engine Private Key | chariotcarts/certs/engine |
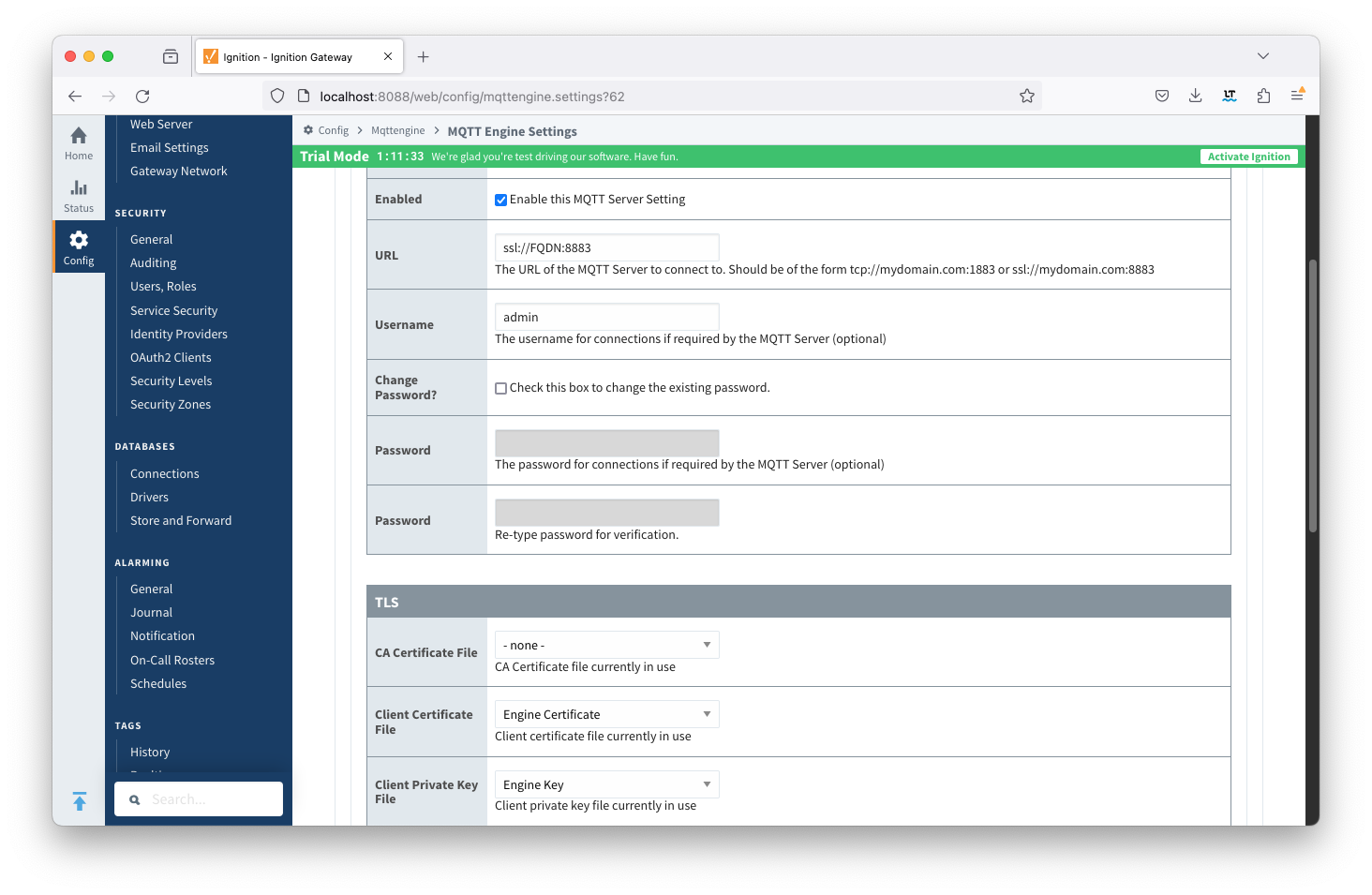
Update the MQTT Engine > Servers > Settings configuration to use the certificates as shown below and setting the URL to be ssl://FQDN:8883 with the FQDN of the Chariot Server. Click the Save Changes button to save the configuration. Note the URL must use SSL. If a non-secure connection is specified here, the connection will not succeed.
| Anchor | ||||
|---|---|---|---|---|
|
Add certificates to the MQTT Transmission
...
| Code Block | ||
|---|---|---|
| ||
clientAuthPolicy="required" |
| Warning |
|---|
| You will now need to restart the Chariot service to pickup up the configuration changes |
...
> Servers > Certificates configuration as shown below:
| Friendly Name | Certificate Filename | File Description | File Location |
|---|---|---|---|
| EngineCertificateTransmissionCertificate | enginetransmission.crt | MQTT Engine Transmission Certificate | chariotcerts/certs/enginetransmisson |
| EngineKeyTransmissionKey | enginetransmission.key | MQTT Engine Transmission Private Key | chariotcartschariotcerts/certs/enginetransmission |
Update the MQTT Engine Transmission > Servers > Settings configuration to use the certificates as shown below and setting the URL to be ssl://FQDN:8883 with the FQDN of the Chariot Serverto use the certificates as shown below. Click the Save Changes button to save the configuration. Note the URL must use SSL. If a non-secure connection is specified here, the connection will not succeed.
...
Add certificates to the MQTT Transmission > Servers > Certificates configuration as shown below:
...
will not succeed.
| Anchor | ||||
|---|---|---|---|---|
|
Chariot MQTT Server still requires MQTT credentials to authenticate incoming client connections, even when using client certificates to set up a TLS/SSL session. If clients will not be sending an MQTT username and password, anonymous connections must be enabled.
To enable anonymous connections, navigate to the Configuration → MQTT Server → Configuration tab and set Allow Anonymous
By default, an anonymous client connection will be allowed to publish and subscribe on # unless the Anonymous MQTT Credentials has been selected.
This will allow you to select any of the configured MQTT Credentials, configured under Configuration → MQTT Credentials, and MQTT Chariot will use the Publish and Subscribe ACLs for that MQTT Credential for all anonymous connections.
| Info |
|---|
| A Password will need to be configured for this MQTT Credential but will not be used by MQTT Chariot |
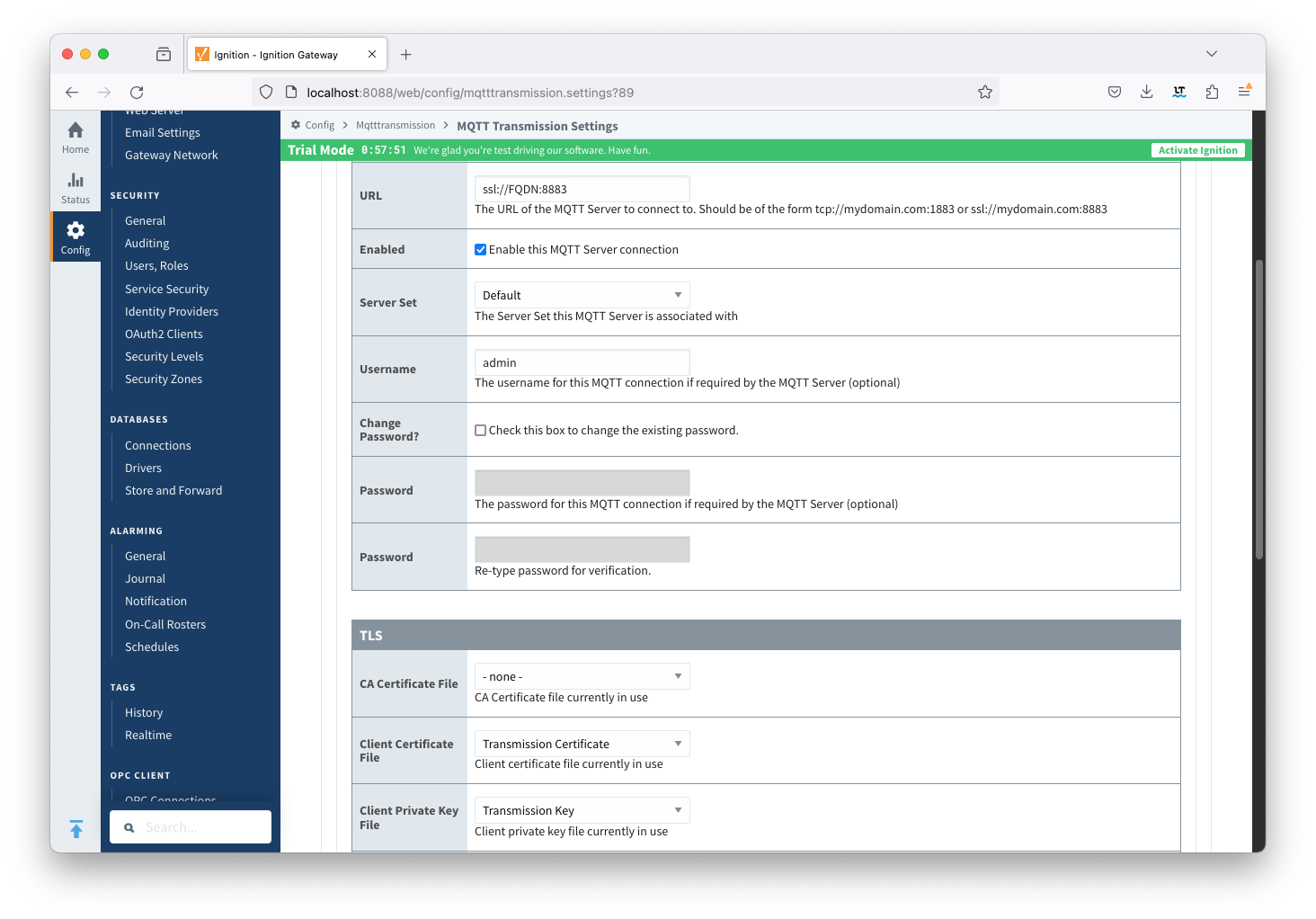
Update the MQTT Transmission > Servers > Settings configuration to use the certificates as shown below. Click the Save Changes button to save the configuration. Note the URL must use SSL. If a non-secure connection is specified here, the connection will not succeed.
...
| Anchor | ||||
|---|---|---|---|---|
|
...