The certificate-based authentication for Azure IoT works like this:
This document details how to create a certificate authority, a root certificate, and the client certificate(s).
The command line tools openssl and keytool are used. Install the OpenSSL command line tool and add the OpenSSL PATH in the Windows environment variables if necessary. Keytool is part of the standard java distribution and is located in the bin sub-directory of your jdk installation directory. Chariot includes a java distribution under the <chariot_install_dir>/lib/runtime/jdk11.0.12_7/bin folder. Add the keytool PATH in the Windows environment variables if necessary. You will need to restart your any open command window to pick up this configuration change. |
As a first step, we need to generate the certificate hierarchy.
Create the following folder structure on your local drive to hold the various certificates in the hierarchy that we will be generating:
iotcerts/
├── rootca/
│ ├── device
On the IoT Hub resource Overview page, click “Certificates” menu on the left blade, and click the “Add” button.

In the “Certificates” blade that appears, give a certficate name (eg. MyOrgIoTHubRootCertificate).
Browse to the IotCerts/rootca folder on your computer and import the rootca.pem. Check the “Set certificate status to verified on upload” checkbox.
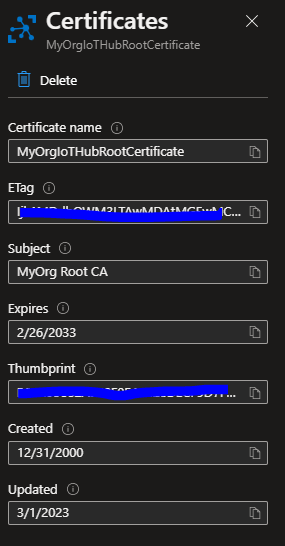
Click Save.
Create Logical Device myiotdevice1
On the resource Overview page, click “Devices” menu on the left blade, and click “Add Device” button.
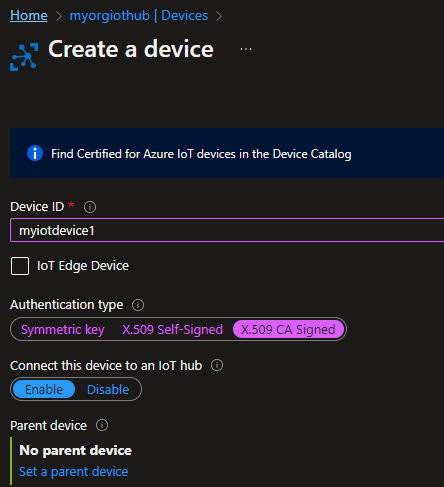
In the “Create a device” page that appears, give myiotdevice1 as the Device Id.
| Note that this name must match the commonName/FQDN we used when generating the client (device) certificate above. |
Select Authentication type X.509 CA Signed. Keep “Connect this device to an IoT Hub” as Enabled.
 it
it
Click Save.