...
This shows a list of the users that are allowed to connect to the MQTT Server. By default, there is only one which is 'admin'. This user is an Instance Admin. There are three different types of usersuser roles:
- Instance Admin
- Is allowed to connect to the MQTT server using the specified ACLs
- Is allowed to make changes to all users in the system (Add, View, Edit, Reset Password, Delete)
- Is allowed to make changes to the VM instance such as setting the hostname, network settings, resetting the trial, uploading a license
- Is not allowed to delete self
- Account Admin
- Is allowed to connect to the MQTT server using the specified ACLs
- Is allowed to make changes to all Account Admin and Account User users in the system (Add, Edit, Reset Password, Delete)
- Is allowed to make changes to the VM instance such as setting the hostname, network settings, resetting the trial, uploading a license
- Is not allowed any operations on Instance Admins - not even view.
- Is not allowed to delete self
- Account User
- Is allowed to connect to the MQTT server using the specified ACLs
- Is not allowed any operations on any other users - not even view.
- Is allowed to Reset Password of self
Basic Usage of Features
- Adding a User
- Users can be added by Instance Admin and Account Admins but the users being added must be at that role level or lower
- Done by clicking 'Add User' which opens the following Window
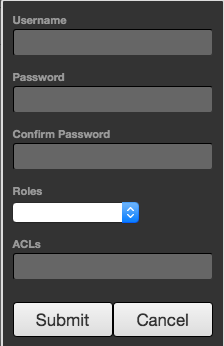 Image Added
Image Added - Username and Password must be set as well as one of the three roles.
- ACLs must be defined. This is a comma separated list of ACLs that define which topics users can publish and subscribe on
ACLs are defined by the following format: [R|W|RW] topic
where:
R = Read or 'subscribe' privileges
W = Write or 'publish' privileges
RW = Read and Write (subscribe and publish) privileges
topic = The topic or wildcard topic representing the scope of the privilege
Below are some example ACL definitions
- RW #
- This allows clients connecting using this username/password to publish and subscribe on any topic
- R #
- This allows clients connecting using this username/password to subscribe on any topic but not publish on any topics
- W #
- This allows clients connecting using this username/password to publish on any topic but not subscribe on any topics
- W device_one/temp/#,R state/#
- This allows clients connecting using this username/password to publish on device_one/temp/# and subscribe on state/# topics
ACLs should be designed with a 'principal of least privilege' model while also considering device management and maintenance. For example gateways and devices in the field should be limited to publishing and subscribing only on the topics for which they should be expected to. The same should be true of 'consumer' applications that will be either sending commands to devices in the field or consuming data coming from those devices.
It is also important to note that a username is not limited to a single MQTT client. A username/password pair could be used for multiple MQTT clients.
If you are new to MQTT topics, Eclipse provides good information here on the basics and wildcards.
- Editing a User
- Resetting a User Password
- Deleting a User
- Reset Trial Timer
- Change Password
- Change Network Settings
- Generate License Request
- Upload License
- Logout
![]()
![]()
![]()
![]()
![]()
![]()
![]()